Active Directory Certificate Templates play a crucial role in establishing trust and security within organizations. By leveraging these templates, organizations can streamline the issuance of digital certificates for various purposes, including authentication, encryption, and digital signatures. To create professional Active Directory Certificate Templates, it is essential to consider several key design elements that convey professionalism and trust.
Template Design Elements
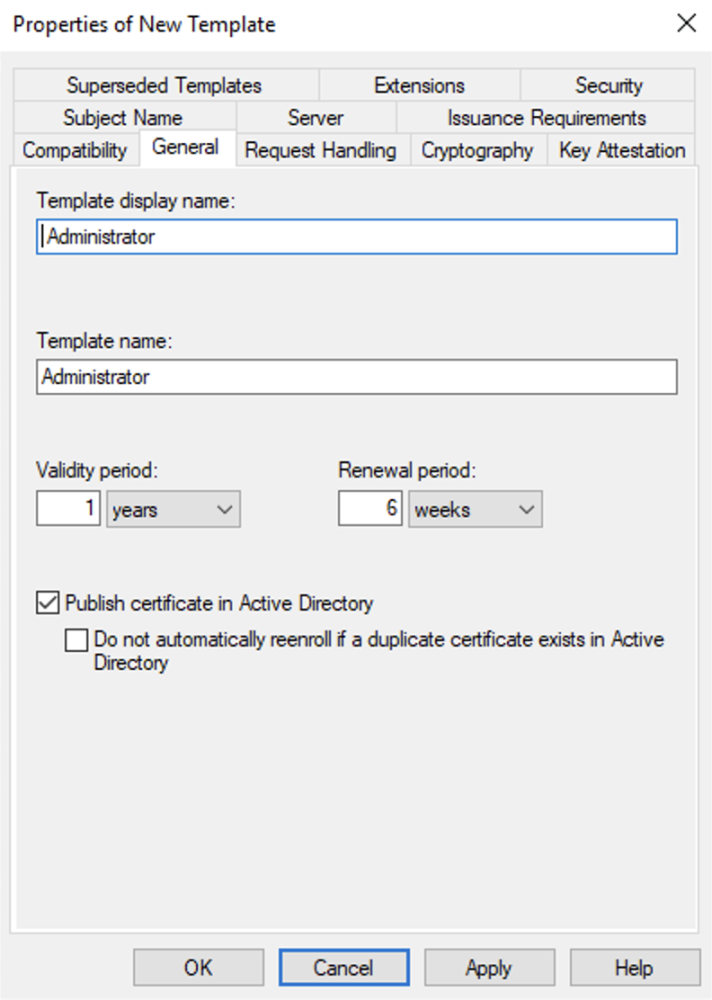
1. Clear and Consistent Branding
Logo Placement: Strategically place the organization’s logo prominently on the template, ensuring it is easily recognizable and aligns with the overall branding.
2. Information Organization
Logical Layout: Arrange information in a logical and intuitive manner, ensuring that key details are easily accessible.
3. Security Features
Watermarks: Incorporate subtle watermarks or background patterns to deter unauthorized use and protect the integrity of the certificate.
4. Certificate Details
Issuer Information: Clearly display the name and contact information of the certificate issuer.
5. Legal and Compliance Requirements
Compliance Standards: Adhere to relevant industry standards and regulations, such as ISO/IEC 27001 or HIPAA, to ensure compliance and maintain trust.
6. User Experience
Accessibility: Design the template to be accessible to individuals with disabilities, ensuring compliance with accessibility standards like WCAG.
7. Customization Options
Variable Data: Allow for the insertion of variable data, such as employee names, department names, or specific certificate details, to personalize each certificate.
Conclusion
By carefully considering these design elements, organizations can create professional Active Directory Certificate Templates that effectively convey trust, security, and professionalism. These templates serve as valuable tools for establishing a strong security posture and protecting sensitive information within the organization.